Privacy Data Breach Policy
The department is committed to protecting the privacy and security of personal information.
This policy outlines how we respond to and manage any data breaches to keep your information safe.
Purpose
This policy upholds the department’s obligation to minimise the risk of the misuse or unauthorised disclosure of personal information, by establishing a clear framework for identifying, managing and responding to data breaches involving personal information.
This policy has been developed in accordance with the:
- Information Privacy Act 2009 (QLD) (IP Act)
- Information Privacy and Other Legislation Amendment Act 2023
- Public Records Act 2023 (QLD)
- Right to Information Act 2009 (QLD)
Authority
An amendment (the amending legislation is the Information Privacy and Other Legislation Amendment Act 2023) to the Information Privacy Act 2009 (Qld) (IP Act) places an obligation on the department to establish processes to implement the Mandatory Notification of Data Breach (MNDB) scheme, applicable as of 1 July 2025.
The MNDB scheme requires the department to take the following prescribed actions in responding to a data breach, including an ‘eligible data breach’:
- immediately take all reasonable steps to contain and mitigate the data breach involving personal information it holds
- if the department does not know whether the data breach is an eligible data breach, assess within 30 days of learning of the breach, whether there are reasonable grounds to believe that the data breach is an eligible data breach
- notify other affected agencies
- if the department reasonably believes or knows or assesses the data breach as an eligible data breach, notify the Office of the Information Commissioner (OIC) and any affected individuals whose personal information is the subject of the data breach, unless an exemption to notification applies.
The MNDB scheme (Section 73 of the IP Act) requires the department to prepare and publish a privacy data breach policy on an accessible agency website, detailing how the department will respond to a data breach including data breaches that are eligible data breaches or suspected eligible data breaches.
Policy statement
The department is committed to protecting the personal information of its customers, staff and other stakeholders and has therefore taken reasonable steps to prevent, detect, respond and recover from data breaches involving personal information, ensuring a robust process to report eligible data breaches as defined in this policy.
In this respect, the department’s information strategy is to enable its employees to make informed decisions, supported by robust policies, procedures and relevant information.
The department has identified 6 key stages in responding to a data breach. While each data breach should be considered on its merits, the data response process illustrated in Figure 1 provides the minimum steps to be considered to support the department in preventing, detecting, responding and recovering from a data breach involving personal information.
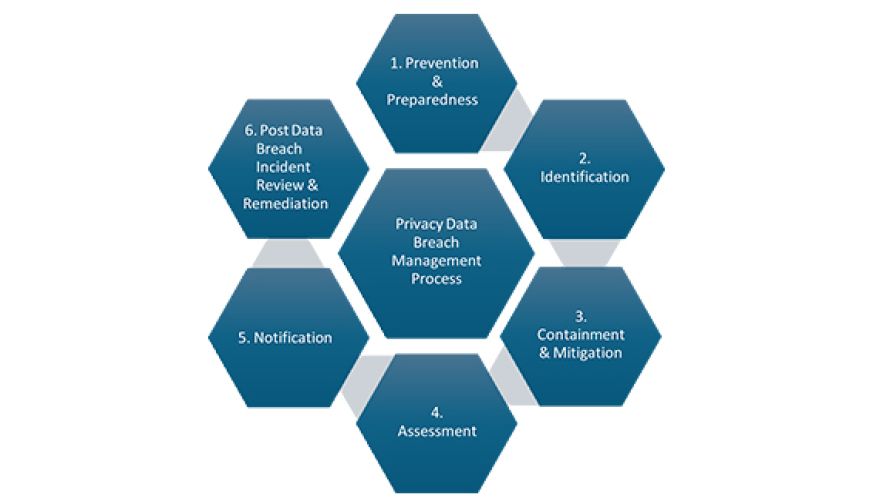
Data breach management process
Prevention and Preparedness
Initial prevention and preparedness are the foundation of the department’s data breach risk management process.
Privacy protections are embedded into systems and processes from the outset as part of a privacy by design approach.
Appropriate risk management processes and capabilities are established during this stage. The department has established governance and operational roles to apply this policy in ensuring compliance to the MNDB scheme.
Clear accountability for privacy data breach management at operational and governance levels has been established.
Personal information risks are regularly assessed and addressed by divisional heads as information owners.
Employees are provided with training to recognise and respond to data breaches. Access to personal data is limited based on business need.
Identification
The identification and reporting of a privacy data breach incident is an essential stage.
All employees have access to training material and corporate knowledge to assist them to promptly identify and report a privacy data breach to line managers for assessment and onward reporting to the RTI and Privacy unit.
All data breach incidents involving personal information must be reported to the department’s RTI and Privacy unit.
Containment and mitigation
The department determines and executes an appropriate strategy to contain and mitigate a data breach of varying and proportionate scale. Timely detection and containment are essential to prevent further harm.
Assessment
The department undertakes a comprehensive assessment of the data breach, including its eligibility and other relevant factors and timeframes as set out under the IP Act and the department’s supporting processes.
Notification
The department ensures processes are in place for prompt notifications under the IP Act. This includes discussions with contracted organisations to ensure coordination of external reporting as required.
The department maintains tested Privacy data breach management processes supported by defined roles and responsibilities.
Post data breach incident review and remediation
In closing out the data breach incident, the department undertakes a review of the incident and considers key lessons, root causes and opportunities that could be implemented as part of a continual improvement focus.
This stage includes addressing data breach requirements in vendor contracts. Detailed records of the breach, decisions made, and actions taken are kept in accordance with recordkeeping requirements.
Open communication with affected stakeholders is maintained to build trust and provide support.
Scope
This policy applies to all employees working for the department regardless of whether they are:
- permanent
- temporary
- full-time
- part-time
- casual employees
- on secondment from another department.
It also applies to other persons who perform work for the department including:
- contractors
- consultants
- third-party suppliers
- vendors
- hosted managed service providers authorised to assess, manage, process or store the department’s information assets and systems
- students gaining work experience and volunteers.
For the purposes of this policy, the term contractor includes on-hired temporary labour services (agency staff).
Delegations
Delegations are to be exercised in accordance with the department’s delegations, including:
- Human Resources
- Financial and Contract
- Legal
- Property
- Building Industry
- Procurement
- Project Commencement
- Administrative.
Roles and responsibilities
The department has identified appropriate roles and responsibilities to give effect to this policy.
Director General (DG)
Responsibilities
- Accountable for the department’s adequate and effective handling of data breaches.
- Sets the privacy compliance culture of the department underpinned by a firm commitment to value and protect personal information.
- Provides strategic leadership and oversight, ensuring effective incident response and recovery.
- Is the information asset(s) owner, unless otherwise specified through policy or a corresponding governance process.
- Is accountable for ensuring the department complies with data governance, legislative, and regulatory requirements.
Director General (DG)
Responsibilities
- Accountable for the department’s adequate and effective handling of data breaches.
- Sets the privacy compliance culture of the department underpinned by a firm commitment to value and protect personal information.
- Provides strategic leadership and oversight, ensuring effective incident response and recovery.
- Is the information asset(s) owner, unless otherwise specified through policy or a corresponding governance process.
- Is accountable for ensuring the department complies with data governance, legislative, and regulatory requirements.
Deputy Director-General (DDG)
Responsibilities
- Has authority and accountability for the confidentiality, integrity and accessibility of information.
- As divisional heads, responsible for the confidentiality, integrity and accessibility controls of information assets, including personal information.
- In stances where the data breach affects more than one division, the DDGs of the impacted divisions will collectively determine how they will coordinate their management of the breach.
- Oversees the management of a data breach that impacts their divisional areas including the determination of a data breach as an eligible data breach and where required, ensures that affected individuals are duly notified of the breach.
- Standing member and leader of the Data Breach Response Team (DBRT).
- Establishes, briefs and coordinates, alternatively delegates the establishment, briefing and coordination, of the DBRT where the data breach has occurred within the DDG’s division.
- Seeks legal advice from the General Counsel as required and, to this end, approves data breach reports issued by their divisions to the Legal unit at the Legal Services branch for legal review and submission to the OIC.
- Ensures that data breaches involving personal information are reported to the RTI and Privacy unit at Legal Services, for regulatory reporting, recording and for compliance guidance.
- Ensures that data breaches involving personal information are adequately and effectively managed and mitigated in accordance with this policy.
Deputy Director-General (DDG)
Responsibilities
- Has authority and accountability for the confidentiality, integrity and accessibility of information.
- As divisional heads, responsible for the confidentiality, integrity and accessibility controls of information assets, including personal information.
- In stances where the data breach affects more than one division, the DDGs of the impacted divisions will collectively determine how they will coordinate their management of the breach.
- Oversees the management of a data breach that impacts their divisional areas including the determination of a data breach as an eligible data breach and where required, ensures that affected individuals are duly notified of the breach.
- Standing member and leader of the Data Breach Response Team (DBRT).
- Establishes, briefs and coordinates, alternatively delegates the establishment, briefing and coordination, of the DBRT where the data breach has occurred within the DDG’s division.
- Seeks legal advice from the General Counsel as required and, to this end, approves data breach reports issued by their divisions to the Legal unit at the Legal Services branch for legal review and submission to the OIC.
- Ensures that data breaches involving personal information are reported to the RTI and Privacy unit at Legal Services, for regulatory reporting, recording and for compliance guidance.
- Ensures that data breaches involving personal information are adequately and effectively managed and mitigated in accordance with this policy.
Data Breach Response Team (DBRT)
Responsibilities
- The DBRT is established, briefed and coordinated by the DDG/ delegate of the affected division, when an eligible data breach is determined by the DDG/delegate.
- A multi-disciplinary team that responds to and manages, in accordance with the department’s Privacy data breach management processes, a data breach that is considered likely to cause serious harm to any impacted individual.
Data Breach Response Team (DBRT)
Responsibilities
- The DBRT is established, briefed and coordinated by the DDG/ delegate of the affected division, when an eligible data breach is determined by the DDG/delegate.
- A multi-disciplinary team that responds to and manages, in accordance with the department’s Privacy data breach management processes, a data breach that is considered likely to cause serious harm to any impacted individual.
Directors, managers and supervisors
Responsibilities
- Identify and escalate concerns within area of responsibility which may enliven the requirements of this policy.
- Immediately report a data breach to the Manager RTI and Privacy and report a breach that is also a cyber security incident to the DTS Service Desk, if not already reported.
- Ensure employees under their supervision are aware of the requirements of this policy.
Directors, managers and supervisors
Responsibilities
- Identify and escalate concerns within area of responsibility which may enliven the requirements of this policy.
- Immediately report a data breach to the Manager RTI and Privacy and report a breach that is also a cyber security incident to the DTS Service Desk, if not already reported.
- Ensure employees under their supervision are aware of the requirements of this policy.
Executive Leadership Team (ELT)
Responsibilities
- Maintain awareness of the policy.
- Ensures that this policy is adequately and effectively applied within the divisions.
- Individuals are delegated by the DG as information owners.
- Report non-compliance with this policy to the RTI and Privacy unit at Legal Services.
Executive Leadership Team (ELT)
Responsibilities
- Maintain awareness of the policy.
- Ensures that this policy is adequately and effectively applied within the divisions.
- Individuals are delegated by the DG as information owners.
- Report non-compliance with this policy to the RTI and Privacy unit at Legal Services.
Employees, consultants, contractors and managed service providers
Responsibilities
- Read and maintain awareness of this policy and its supporting processes to understand what is expected of them.
- Comply with the IP Act, including protecting personal information held by the department from unauthorised access, disclosure or loss.
- Recognise a data breach and promptly report it.
- Where required, and in accordance with this policy, immediately report a data breach or suspected data breach to their line manager. Managed service providers report data breaches to the contract contact person as detailed in their contractual arrangements with the department.
- In consultation with line managers, employees complete the Privacy data breach report form and submit to the Manager RTI and Privacy.
- Respond to requests for information from and cooperate with line managers, the Manager RTI and Privacy and/or the DBRT.
- Comply with record keeping and reporting obligations.
Employees, consultants, contractors and managed service providers
Responsibilities
- Read and maintain awareness of this policy and its supporting processes to understand what is expected of them.
- Comply with the IP Act, including protecting personal information held by the department from unauthorised access, disclosure or loss.
- Recognise a data breach and promptly report it.
- Where required, and in accordance with this policy, immediately report a data breach or suspected data breach to their line manager. Managed service providers report data breaches to the contract contact person as detailed in their contractual arrangements with the department.
- In consultation with line managers, employees complete the Privacy data breach report form and submit to the Manager RTI and Privacy.
- Respond to requests for information from and cooperate with line managers, the Manager RTI and Privacy and/or the DBRT.
- Comply with record keeping and reporting obligations.
General Managers and Executive Directors
Responsibilities
- In consultation with the DDG, determines whether the breach is an eligible data breach by assessing the severity of the breach involving personal information and the likelihood that the breach will result in serious harm to an individual to whom the information involved relates.
- Assists the affected business area to identify suitable members to form part of the DBRT where the breach involves information management systems and has been assessed to cause serious harm to affected individuals.
- Under the guidance of the DDG, notifies affected individuals of the data breach.
General Managers and Executive Directors
Responsibilities
- In consultation with the DDG, determines whether the breach is an eligible data breach by assessing the severity of the breach involving personal information and the likelihood that the breach will result in serious harm to an individual to whom the information involved relates.
- Assists the affected business area to identify suitable members to form part of the DBRT where the breach involves information management systems and has been assessed to cause serious harm to affected individuals.
- Under the guidance of the DDG, notifies affected individuals of the data breach.
Information Custodians
Responsibilities
- In accordance with this policy and the Data governance policy, ensures legislative, regulatory and policy compliance in relation to the protection and storage of personal information.
Information Custodians
Responsibilities
- In accordance with this policy and the Data governance policy, ensures legislative, regulatory and policy compliance in relation to the protection and storage of personal information.
Directors, managers and supervisors
Responsibilities
- Identifies and escalate concerns within area of responsibility which may enliven the requirements of this policy.
- Immediately reports a data breach to the Manager RTI and Privacy and report a breach that is also a cyber security incident to the DTS Service Desk, if not already reported.
- Ensures employees under their supervision are aware of the requirements of this policy and its supporting processes.
Directors, managers and supervisors
Responsibilities
- Identifies and escalate concerns within area of responsibility which may enliven the requirements of this policy.
- Immediately reports a data breach to the Manager RTI and Privacy and report a breach that is also a cyber security incident to the DTS Service Desk, if not already reported.
- Ensures employees under their supervision are aware of the requirements of this policy and its supporting processes.
RTI and Privacy unit
Responsibilities
- Provides privacy compliance advice to the department.
- Guides the business areas in their assessment of the severity of a data breach involving personal information and the likelihood that a breach will result in serious harm to an individual to whom the information.
- Updates and maintains this policy and its supporting processes.
- Educates employees about data breaches and recommends improvement to processes that will reduce the risk of future incidents.
RTI and Privacy unit
Responsibilities
- Provides privacy compliance advice to the department.
- Guides the business areas in their assessment of the severity of a data breach involving personal information and the likelihood that a breach will result in serious harm to an individual to whom the information.
- Updates and maintains this policy and its supporting processes.
- Educates employees about data breaches and recommends improvement to processes that will reduce the risk of future incidents.
Human rights
A Record for Assessing Compatibility with Human Rights has been completed to demonstrate how human rights have been considered in the development of this policy.
The policy does not engage or limit any human right under the Act therefore it is reasonable to conclude the policy is compatible with human rights.
Contact
For further information, email the General Counsel at legalrequests@epw.qld.gov.au.
Storage of information
All information should be managed in accordance with the Public Records Act 2023, and the whole-of-Government Records governance policy.
In addition, personal information should be managed in accordance with the Information Privacy Act 2009.
Document control
- Document owner: General Counsel, Legal Services
- Contact details: legalrequests@epw.qld.gov.au
- Next review: June 2027
- Supersedes: N/A
- Version: 1.0
- Issue date: 1 September 2025
- Reason: New document
- Author: Project Manager Privacy, Legal Services, Corporate Services
- Approver: Deputy Director General, Corporate Services
- Licence: Privacy data breach policy © The State of Queensland (Department of Housing and Public Works) 2025.
Appendix A: Additional contacts and information
Contact
Right to Information and Privacy unit
Legal Services branch
Corporate Services division
Email: RTI-Privacy@hpw.qld.gov.au
Phone: (07) 3008 3119
Information
In addition to the documents mentioned in section 2 Authority, the requirements set out in this document are consistent with relevant Government legislation, regulations, directives, information standards and/or policies at the time of publication. Supporting information is available.
Legislation and regulations
- Information Privacy Act 2009 (QLD) (IP Act)
- Information Privacy and Other Legislation Amendment Act 2023
- Public Records Act 2023 (QLD)
- Right to Information Act 2009 (QLD)
- Public Interest Disclosures Act 2010 (QLD)
Queensland Government documents
Relevant Queensland Government documents that the policy relates to or that help support understanding and action under this policy
- Whole of Government Records Governance policy
- IPOLA Guideline: MNDB Scheme (Office of the Information Commissioner)
- QGEA Information Governance Policy
Appendix B: Definitions
Aligned with the definitions in the IP Act, these are the key terms referred to in this policy.
Affected individual
An individual who is at risk when a data breach occurs involving their personal information, in that they are likely to suffer serious harm as a result of the data breach. Affected individuals could include department customers, housing applicants, tenants and employees.
Delegate
The person authorised to perform a specific task or function on the Director General or Minister’s behalf. Delegations and authorisations are recorded in the department’s delegation schedules.
Privacy data breach
The unauthorised access or disclosure of information held by the department or the loss of personal or non-personal information held by the department where unauthorised access or disclosure is likely to occur (OIC IPOLA Guideline MNDB Assessing a Data Breach, Page 4).
Examples of incidents that can lead to a data breach include:
- loss of a department work phone or laptop
- human error
- malicious
- criminal cyber-attacks.
Privacy data breach report form
A reporting template used by employees to document and report the data breach involving personal information to line managers and to the RTI and Privacy unit for assessment and further notifications.
Eligible data breach
The concept of an eligible data breach* requires both of the following requirements to be satisfied:
- There is unauthorised access to, or unauthorised disclosure of, personal information held by the department, or there is a loss of personal information held by the department in circumstances where unauthorised access to, or unauthorised disclosure of, the information is likely to occur.
- The unauthorised access or disclosure of the information is likely to result in serious harm to an individual (refer Section 47(1) of the IP Act).
*Includes a suspected eligible data breach.
Exemption to notification
The department is not required to notify* individuals, however, must still notify the OIC in the following instances (refer Section 50(2) of the IP Act).
- The department has taken remedial action to mitigate the breach, so that the breach is no longer likely to result in serious harm to any individual.
- Notifying an individual would create a serious risk of harm to an individual’s health or safety.
- Notifying an individual is likely to compromise or worsen the department’s cybersecurity or lead to further data breaches.
* The department is exempt from notifying both the individual and the OIC to the extent that providing notifications otherwise required:
- would likely prejudice an investigation that could lead to the prosecution of an offence, or proceedings before a court or tribunal
- will result in a duplication of notifications in an instance of multiple agency breach involving the same incident, and where at least of the agencies has undertaken to notify individuals and the OIC6.
Personal information
Information or an opinion about an identified individual or an individual who is reasonably identifiable from the information or opinion:
- whether the information or opinion is true or not
- whether the information or opinion is recorded in a material form or not.
Serious harm
To an individual in relation to the unauthorised access or unauthorised disclosure of the individual’s personal information, includes, for example:
- serious physical, psychological, emotional or financial harm* to the individual because of the access or disclosure
- serious harm to the individual’s reputation because of the access or disclosure.
*Occurs where the harm arising from the eligible data breach has, or may, result in a real and substantial detrimental effect to the individual. The effect on the individual must be more than mere irritation, annoyance or inconvenience.
Section 47(2) of the IP Act prescribes factors to consider when assessing whether the likely harm is 'serious harm'. These factors include:
- the kind of personal information disclosed
- sensitivity of the personal information involved
- the persons who have or may have obtained the personal information subject to the breach.